Die Terrapin-Attacke hat Ende 2023 nochmal richtig für Aufruhr gesorgt und offenbarte einer der größten Schwachstellen im SSH-Protokoll bis dato. So beunruhigend das auch für jeden Administrator sein mag, das erfolgreiche Ausnutzen dieser Schwachstelle stellt sich als äußerst komplex heraus – Die Schutzmaßnahmen allerdings sind sehr einfach umzusetzen.
Attention: For the english version, click here!
Die Forscher der Ruhr Universität Bochum, die diesen Angriffsvektor aufgedeckt haben, entwickelten dafür den Terrapin-Scanner. Dieser prüft, ob deine SSH-Konfiguration potenziell anfällig ist für die Terrapin-Attacke. Dieser Angriff kann dazu führen, dass ein verschlüsselter Verbindungsaufbau unsicher wird. Um Client und Server davor zu schützen muss Chacha20 und ETM-basierte MACs deaktiviert werden. Diese Überprüfung nimmt der Scanner für dich vor.
Terrapin-Scanner herunterladen und ausführen
Du hast die Möglichkeit den Scanner selbst zu kompilieren – hier geht’s zum GitHub Repository – oder für die geläufigsten Betriebssysteme eine vorkompilierte Version hier herunterzuladen.
Für mein Linux-Testsystem habe ich mir den Terrapin_Scanner_Linux_amd64 heruntergeladen.
cd /home/dennis/Downloads
./Terrapin_Scanner_Linux_amd64 -connect 127.0.0.1Das Ergebnis des Scanners sieht wie folgt aus:
================================================================================
==================================== Report ====================================
================================================================================
Remote Banner: SSH-2.0-OpenSSH_8.9p1 Ubuntu-3ubuntu0.6
ChaCha20-Poly1305 support: true
CBC-EtM support: false
Strict key exchange support: true
The scanned peer supports Terrapin mitigations and can establish
connections that are NOT VULNERABLE to Terrapin. Glad to see this.
For strict key exchange to take effect, both peers must support it.
Note: This tool is provided as is, with no warranty whatsoever. It determines
the vulnerability of a peer by checking the supported algorithms and
support for strict key exchange. It may falsely claim a peer to be
vulnerable if the vendor supports countermeasures other than strict key
exchange.
For more details visit our website available at https://terrapin-attack.comDas Ergebnis sagt aus, dass ChaCha20 unterstützt wird, CBC-EtM hingegen nicht. Dem sollte ich also entgegensteuern, um einen möglichen Angriff zu vermeiden.
Um ChaCha20 zu deaktivieren, öffne die Datei /etc/ssh/sshd_config und füge am Ende der Datei folgendes ein:
Ciphers -chacha20-poly1305@openssh.comStarte den SSH-Daemon danach neu und führe den den Scanner erneut aus:
service ssh restart
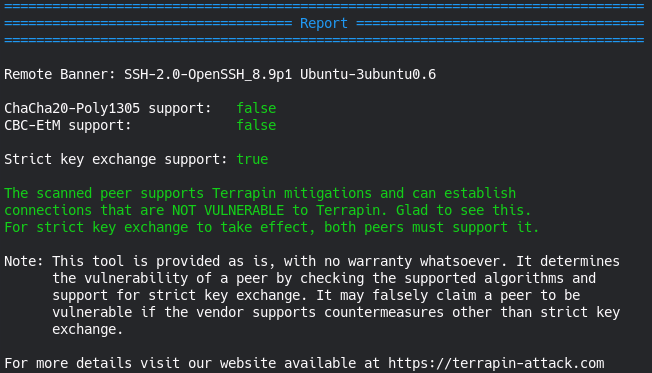
./Terrapin_Scanner_Linux_amd64 -connect 127.0.0.1Jetzt ist ChaCha20 systemweit deaktiviert, wie der Report uns mitteilt:
================================================================================
==================================== Report ====================================
================================================================================
Remote Banner: SSH-2.0-OpenSSH_8.9p1 Ubuntu-3ubuntu0.6
ChaCha20-Poly1305 support: false
CBC-EtM support: false
Strict key exchange support: true
The scanned peer supports Terrapin mitigations and can establish
connections that are NOT VULNERABLE to Terrapin. Glad to see this.
For strict key exchange to take effect, both peers must support it.
Note: This tool is provided as is, with no warranty whatsoever. It determines
the vulnerability of a peer by checking the supported algorithms and
support for strict key exchange. It may falsely claim a peer to be
vulnerable if the vendor supports countermeasures other than strict key
exchange.
For more details visit our website available at https://terrapin-attack.comZusammenfassung
Abschließend ist zu sagen, dass natürlich kein Scanner eine hundertprozentige Sicherheit gibt. Es ist ein nützliches Tool, um seine Systeme zu überprüfen, dennoch sollten die SSH Konfigurationen durch einen Administrator nochmals geprüft werden. Allerdings An der Stelle ist auch nochmal wichtig zu sagen, dass Client und Server entsprechend konfiguriert sein müssen, um den Angriffsvektor ausschließen zu können.
Für Vendor Fixes und ausführliche Informationen rund um die Terrapin-Attacke, empfehle ich terrapin-attack.com zu besuchen.
Weitere Quellen
Die dazugehörigen CVE’s zum Nachlesen:
- CVE-2023-48795: General Protocol Flaw
- CVE-2023-46445: Rogue Extension Negotiation Attack in AsyncSSH
- CVE-2023-46446: Rogue Session Attack in AsyncSSH
https://www.linuxglobal.com/thwarting-the-terrapin-ssh-attack/
Terrapin-Scanner checks SSH connections
The Terrapin attack caused quite a stir at the end of 2023, revealing one of the most significant vulnerabilities in the SSH protocol to date. As alarming as this may be for any administrator, exploiting this vulnerability successfully proves to be extremely complex. However, the protective measures are relatively simple to implement.
Researchers at Ruhr University Bochum, who uncovered this attack vector, developed the Terrapin Scanner for this purpose. It checks whether your SSH configuration is potentially vulnerable to the Terrapin attack, which could compromise the security of an encrypted connection. To protect both client and server, Chacha20 and ETM-based MACs must be disabled, and the scanner performs this verification for you.
Download and Run the Terrapin-Scanner
You have the option to compile the scanner yourself (GitHub Repository link) or download a precompiled version for the most common operating systems here.
For my Linux test system, I downloaded the Terrapin_Scanner_Linux_amd64:
cd /home/dennis/Downloads
./Terrapin_Scanner_Linux_amd64 -connect 127.0.0.1The scanner’s result appears as follows:
================================================================================
==================================== Report ====================================
================================================================================
Remote Banner: SSH-2.0-OpenSSH_8.9p1 Ubuntu-3ubuntu0.6
ChaCha20-Poly1305 support: true
CBC-EtM support: false
Strict key exchange support: true
The scanned peer supports Terrapin mitigations and can establish
connections that are NOT VULNERABLE to Terrapin. Glad to see this.
For strict key exchange to take effect, both peers must support it.
Note: This tool is provided as is, with no warranty whatsoever. It determines
the vulnerability of a peer by checking the supported algorithms and
support for strict key exchange. It may falsely claim a peer to be
vulnerable if the vendor supports countermeasures other than strict key
exchange.
For more details visit our website available at https://terrapin-attack.comThe result indicates that ChaCha20 is supported, but CBC-EtM is not. To address this, you should disable ChaCha20. Open the file /etc/ssh/sshd_config and add the following line at the end:
Ciphers -chacha20-poly1305@openssh.com
Restart the SSH daemon and run the scanner again:
service ssh restart
./Terrapin_Scanner_Linux_amd64 -connect 127.0.0.1Now, as the report shows, ChaCha20 is disabled system-wide:
================================================================================
==================================== Report ====================================
================================================================================
Remote Banner: SSH-2.0-OpenSSH_8.9p1 Ubuntu-3ubuntu0.6
ChaCha20-Poly1305 support: false
CBC-EtM support: false
Strict key exchange support: true
The scanned peer supports Terrapin mitigations and can establish
connections that are NOT VULNERABLE to Terrapin. Glad to see this.
For strict key exchange to take effect, both peers must support it.
Note: This tool is provided as is, with no warranty whatsoever. It determines
the vulnerability of a peer by checking the supported algorithms and
support for strict key exchange. It may falsely claim a peer to be
vulnerable if the vendor supports countermeasures other than strict key
exchange.
For more details visit our website available at https://terrapin-attack.comConclusion
In conclusion, it’s important to note that no scanner provides absolute security. It is a useful tool to inspect one’s systems, nevertheless, the SSH configurations should also be reviewed by an administrator. It’s crucial to configure both client and server appropriately to mitigate the attack vector.
More Ressources
For vendor fixes and detailed information about the Terrapin attack, visit terrapin-attack.com
Additionally, refer to the associated CVEs for further reading:
- CVE-2023-48795: General Protocol Flaw
- CVE-2023-46445: Rogue Extension Negotiation Attack in AsyncSSH
- CVE-2023-46446: Rogue Session Attack in AsyncSSH
https://www.linuxglobal.com/thwarting-the-terrapin-ssh-attack/
Start the discussion